What Is DORA and Why?
DORA (Digital Operational Resilience Act) targets all financial entities within the EU such as banks, insurance companies and investment funds with specific requirements regarding their digital operational resilience. The core of DORA includes ICT risk management, including cybersecurity, data governance and business continuity management.
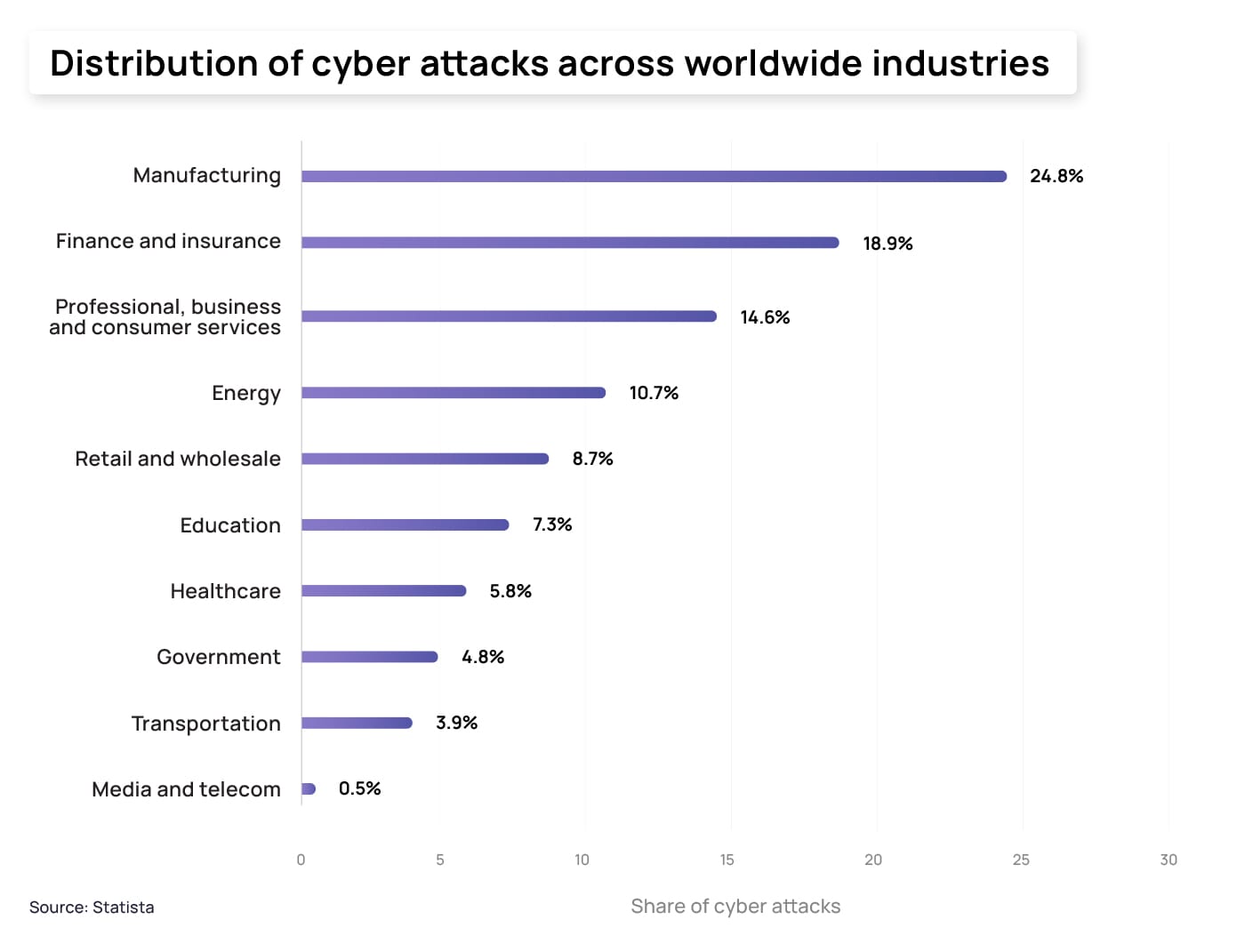
With increasing interconnectedness and digitization in the financial sector, the risk of cyber attacks is also growing. Statista reported that the financial and insurance sector was one of the top targets for cybercriminals in 2022, highlighting its vulnerability to digital threats.
↓
5 Important Elements Of DORA
Financial institutions should implement robust mechanisms for identifying, assessing, and mitigating ICT risks.
There should be a detailed process for reporting significant cyber incidents to relevant regulators.
Regular testing of digital infrastructure to verify resilience against various types of failures and attacks.
Strict rules for managing the risks associated with outsourcing ICT services, including the requirement for contractual and audit rights.
A framework for establishing a secure ICT environment, including adequate management of ICT assets, data integrity, and protection against data breaches.
Request a Dora Audit!
Contact Info
- info@dpoassociates.eu
- legal@dpoassociates.eu
Please fill out the form below and we will contact you as soon as possible!
How to Comply with DORA.
Develop risk management policies
Financial institutions should begin developing comprehensive ICT risk management policies that encompass all aspects of digital operational resilience. These policies should be regularly reviewed and updated to meet the changing technological and threat landscapes.
Implementation of Strong Cybersecurity Measures
Implementing advanced cybersecurity technologies and practices is critical. This includes the use of firewalls, antivirus programs, intrusion detection systems, and regular security audits.
Training and Awareness
Raising awareness and training staff in cybersecurity and digital resilience best practices is essential. Employees need to be aware of the potential risks and how they can help strengthen operational resilience.
Testing and Recovery Planning
Regular testing of systems for resilience against failures and attacks helps identify vulnerabilities. In addition, it is essential to have an effective recovery plan that kicks in after an incident to ensure business continuity.
Management of Third Parties
Managing relationships with third-party ICT service providers requires thorough due diligence and continuous monitoring. Contracts should contain clear and enforceable provisions regarding compliance with DORA requirements.
Information Exchange About Cyber-threads And Vulnerability
Organizations are required to submit three separate reports for critical incidents: an initial notification to notify authorities, an interim report on the progress of incident resolution, and a final report analyzing the root causes of the incident.
Start DORA Implementation Yourself!
Leave your contact information and we’ll send you the DORA information registry!
The information register is part of the third-party ICT risk management framework and enables financial entities to identify and assess risks related to contractual arrangements for the use of ICT services.

