Introduction
The NIS2 directive requires organizations to meet strict cybersecurity requirements. But how do you know where your organization stands? Evaluating your current measures is the first step toward compliance. In this blog, we offer practical tips to get an overview of what you’re already doing well and where your areas for improvement lie. Whether you’re a start-up SME or an experienced IT professional, this guide will help you move forward.
1. Map your digital assets
To start, you need to know what you are protecting. Take an inventory of all the systems, networks and devices that make up your digital infrastructure. Remember: the NIS2 directive emphasizes critical and essential infrastructure.
Not sure if your business falls into essential or critical? Check it out here!
Checklist:
- Servers, databases and cloud environments
- Workstations and mobile devices
- Networking and firewalls
- Software applications and SaaS tools.
2. Analyze existing security measures
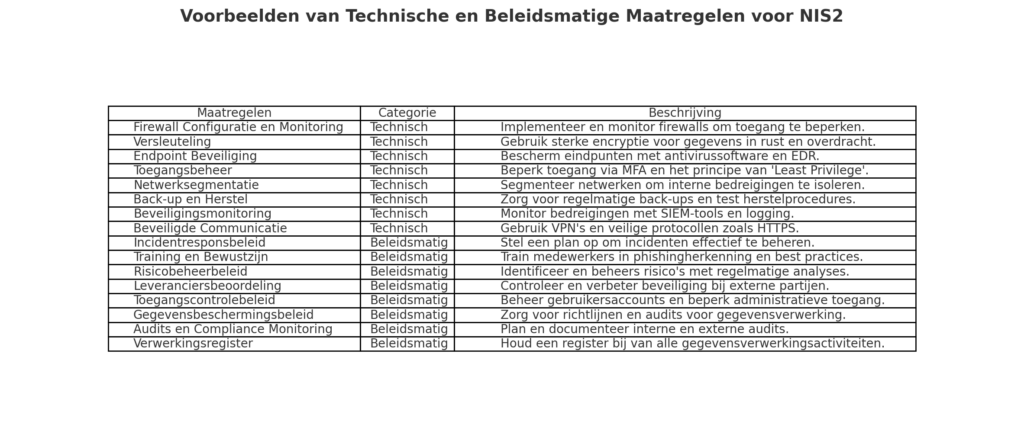
Examine what cybersecurity measures you have already implemented. This includes both technical solutions and policies. Ask yourself: do these meet the minimum security requirements of NIS2?
Important questions to answer:
- Are your firewalls and antivirus programs up to date?
- Do you use encryption for sensitive data?
- Do you have an access policy that prevents unauthorized access to systems?
- Are backup systems in place to recover data in the event of an incident?
3. Conduct a risk analysis
The NIS2 directive requires organizations to proactively identify and manage risks. List potential threats, assess their likelihood of occurrence and impact.
Steps for a simple risk analysis:
- Identify risks: For example, phishing, ransomware, or insider threats.
- Assess the impact: What will happen if this risk occurs? Consider financial damage, loss of reputation, and legal consequences.
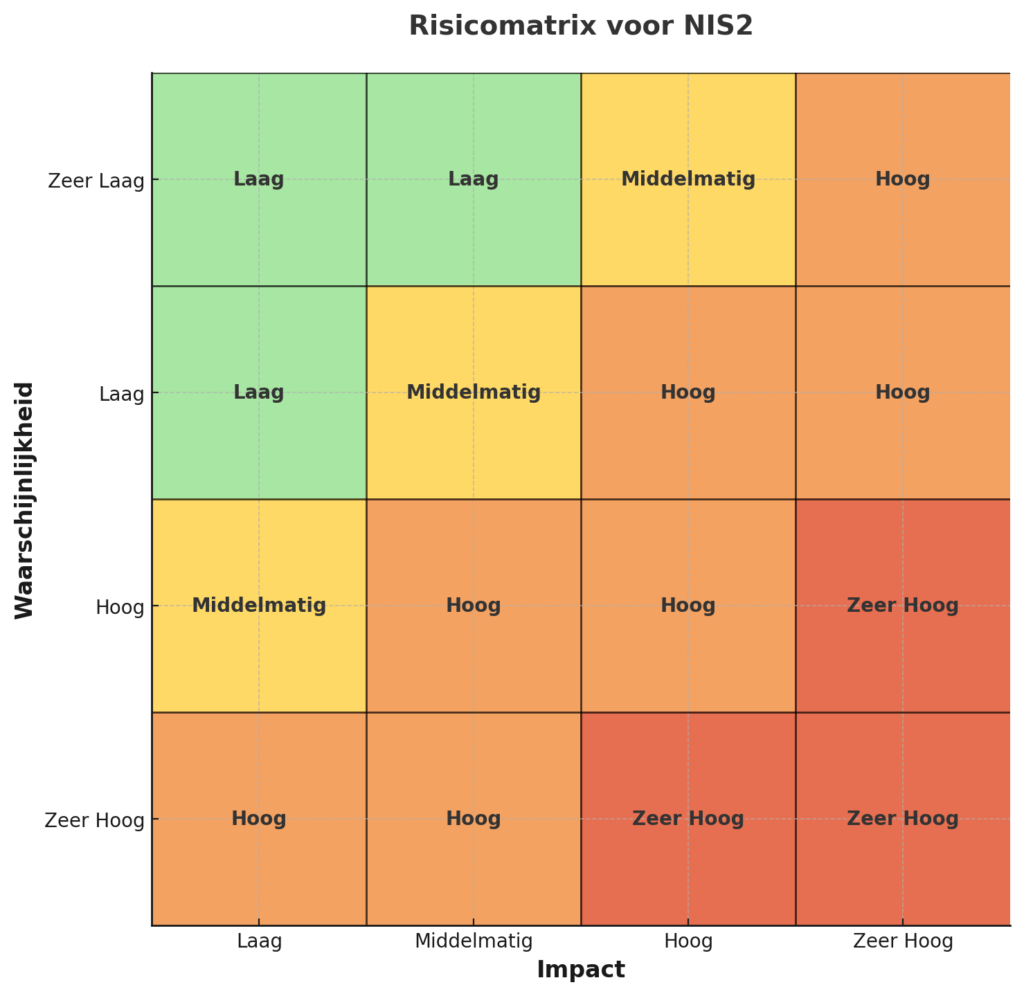
- Rank risks: Use a matrix to prioritize.
The example risk matrix shows how risks can be ranked by probability (vertical axis) and impact (horizontal axis), color-coded from green (low risk) to red (very high risk).
4. Test your incident response plan
An incident response plan is one of the key requirements under NIS2. Do you already have a plan? Test it regularly to see if it works.
To-do:
- Practice a scenario, such as a data breach or ransomware attack.
- Check that all involved understand their tasks.
- Measure how quickly your organization can respond and recover.
5. Evaluate training and awareness within the team
Employees are often the weakest link in cybersecurity. Make sure your team is aware of cyber threats and knows how to act.
Questions to ask:
- Have your employees taken recent training on phishing and password management?
- Are there clear guidelines for reporting suspicious activity?
- Is there regular testing such as phishing simulations?
6. Work with an outside expert
For many organizations, an outside party, such as a DPO (Data Protection Officer), can help assess compliance and implement improvements. This can be especially helpful if you don’t have the resources to do this internally.
Advantages:
- NIS2 compliance expertise.
- Saving time and internal resources
- An objective look at your current measures
Not sure if your organization is ready for NIS2? Request a free consultation and get instant insight into your compliance level.
Conclusion
Evaluating your current cybersecurity measures for NIS2 compliance does not have to be a complicated process. By following a structured approach, you’ll quickly gain insight into your strengths and areas for improvement. Need help with the process? Contact us for a free consultation.









